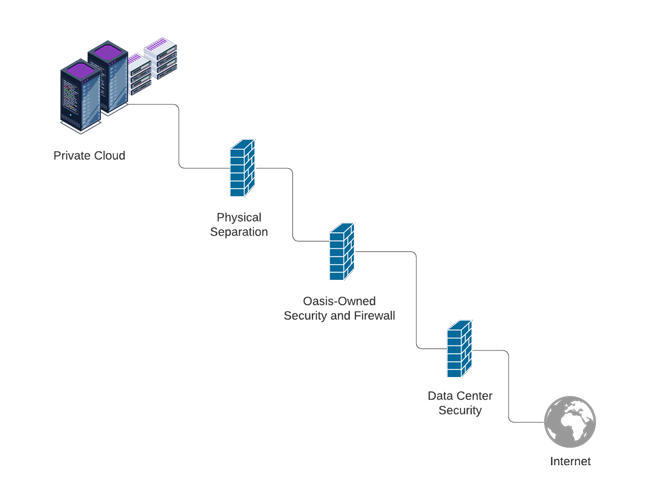
Features
Physically isolated
Advanced encryption
Cabinet access
Predictable cost
Audit and compliance
Hypervisor control

Benefits
Separated infrastructure for additional protection
Client-managed encryption keys for ultimate compliance
Access to your servers at any time
Forecast your budget with absolute certainty
Additional access to configuration and access logs
Enhanced control over resource allocation and virtualization options